When Hardware Gets Hostile: The Rise of DMA Game Hacking
Why memory level attacks are escalating the anticheat arms race? Direct Memory Access (or known as DMA) cheats use hardware based memory access to bypass conventional anticheat systems. As traditonal defense tighten against software cheats and AI driven hacks, some attackers are turning to DMA because it operates outside the monitored software environment, making detection extremely difficult. This trend compounds the challenges of AI enabled cheats and reinforces the need for multi layered, hardware aware defenses, including some of the ideas introduced on our recent post on visual AI anticheat solutions like Waldo.
What is DMA game hacking?
Direct Memory Access (DMA) is a legitimate computer mechanism that allows certain hardware devices (like network cards or storage controllers) to transfer data to and from system memory without involving the CPU. In the context of game cheating, attackers repurpose this capability to read (and in some setups write) game memory directly, bypassing the CPU and operating system supervision entirely. Because anticheat systems primarily monitor CPU mediated processes, DMA cheating can evade those mechanisms.
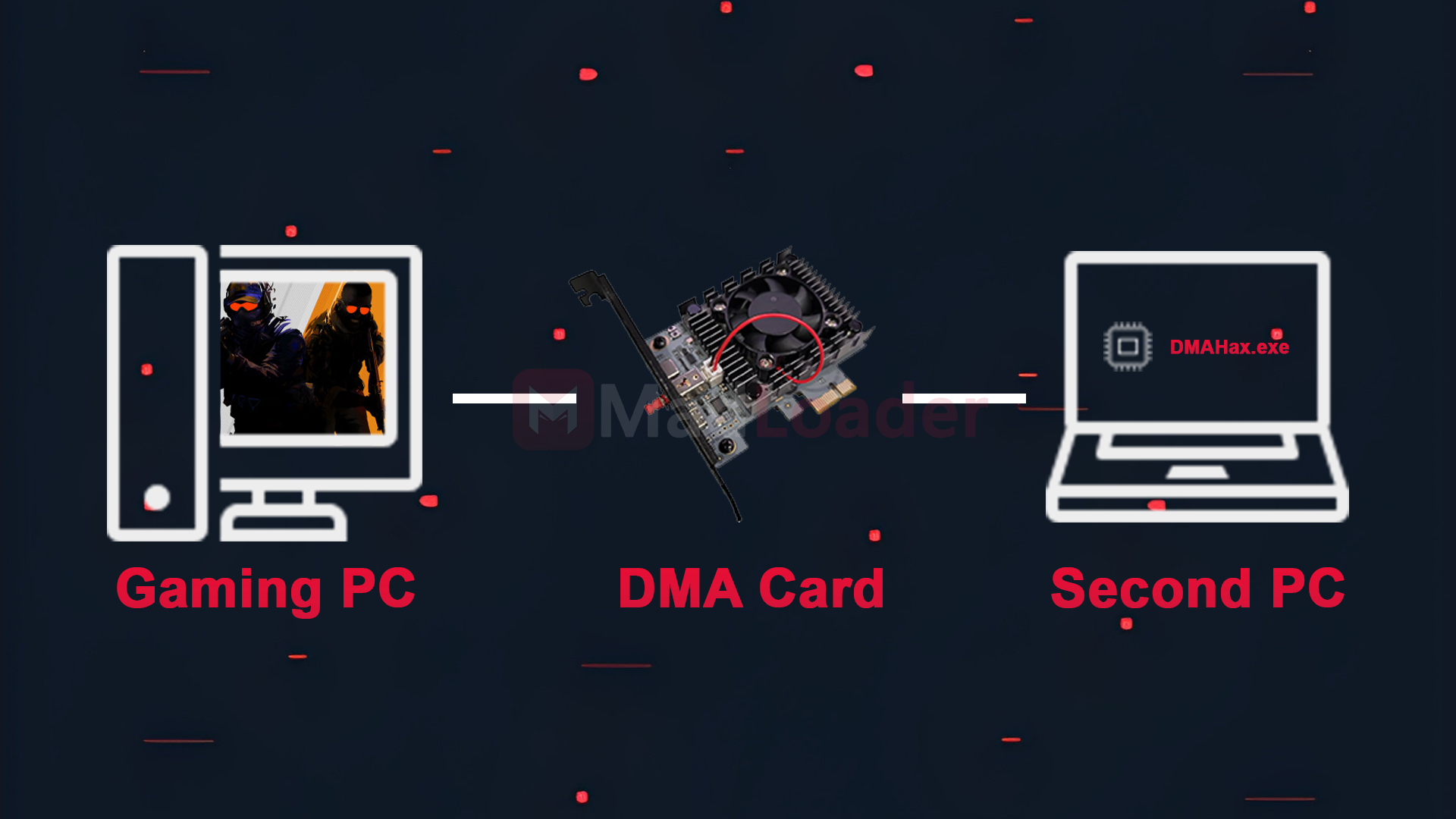
How a typical DMA cheat is setup:
- A specialized PCIe device (or other high speed interface) is plugged into the gaming PC.
- That device connects to a second computer that runs the cheat logic and interprets memory state.
- The main gaming PC has no cheat software installed, meaning traditional scans and hooks see nothing suspicious.
Why DMA is attractive to cheat developers
1. Anticheat systems can’t see/detect it Because DMA operates at a hardware level outside of the operating system, conventional anticheat tools, even kernel level ones like Vanguard or BattlEye often cannot monitor or intercept its activity. This makes DMA cheats effectively invisible to software based detection unless specialized hardware monitoring is in place.
2. No local cheat binaries Standard anticheat approaches scan proceses, drivers, and memory writes for known cheat signatures. DMA setups never run the cheat on the machine itself, so there are no processes to scan, no injections to detect, and no suspicious driver files to flag.
3. Real-time memory access DMA can read game state like player positions, health values, hitboxes in real time with minimal latency, providing rich data for features like aimbots, esp, no recoil or any that is possible to exploit. This physical layer access is fundamentally different from external software cheats that still rely on OS mediated memory reads.
How DMA cheats are actually deployed
Common DMA setups often use a two-system architecture:
- Main gaming PC: Runs the game normally. No cheat software present.
- Secondary system: Connected via USB to the DMA device; runs cheat that reads memory, interprets game state, and sends input or overlay data back to the main.
Complementary hardware like KMbox (which emulate mouse/keyboard input) and fusers (which combine video output from the secondary system) help make the cheat seamless without leaving detectable traces on the primary system.
What DMA cheats enables in practice
Because DMA accesses raw memory, attackers can build features that are extremely hard to implement with software alone:
- Wallhacks/ESP: by reading entity positions and visibility data.
- Aimbots with precision targeting: using real state information.
- Speed or physics manipulation: where memory values affect gameplay variables.
- Radar or overlay applications: fed from direct memory analytics.
- In Game Weapon Manipulation: manipulates weapon behavior like no recoil, no spread or bullet trace. This is similar to what AI cheat models do but with real, high fidelity internal data, making automated strategies far more accurate and harder to distinguish from legitimate play.
Why DMA is especially hard to detect?
Traditional anticheat systems operate in the OS or CPU context, scanning processes, drivers, and hooks. DMA cheats bypass that entirely because the access occurs at the hardware bus level, so there is often no software event to flag. This means:
- No executable pattern to blacklist.
- No unusual driver to scan.
- No memory injection signature.
- No local telemetry for behavioral analysis unless derived indirectly. The only signals available may be subtle system irregularities or game level behavior anomalies, but distinguihing those from expert play remains difficult.
Connections to AI cheat evolution
Our previous posts on the future of AI game hacking showed how machine learning models can create more human like cheat behavior, evading detection by mimicking variability. DMA feeds those models with high fidelity state data, making AI cheats more accurate and harder to distinguish from legitimate play behavior.
The Waldo visual AI anticheat approach analyzing rendered frames for suspicious patterns becomes incredibly relevant here, because it operates on output rather than process internals, Waldo style detection could flag anomalies even when memory access is hidden. Visual analysis and behavioral heuristics can catch what hardware based cheats try to hide from software monitors.
Thus, to defend against DMA and AI cheating, a multi layered approach that includes serverside behavior analysis, visual detection systems, and hardware signal monitoring becoes necessary.
Emerging industry responses
Some modern anticheat systems (ex. Riot’s Vanguard) work on kernel level drivers capable of monitoring unauthorized memory calls and even blocking suspicious DMA hardware access. This indicates a shift toward platform aware defenses that combine software signatures with hardware bus monitoring.
Other research suggests using behavioral biometrics or server side consistency checks to identify anomalies that hardware cheats cannot hide even if local detection fails. This is similar in spirit to AI models that classify playstyle rather than execution artifacts.
Conclusion: a new frontier in the cheat arms race
DMA cheating represents a significant escalation in cheat sophistication because it bypasses the very layer where most anticheat systems operate. When combined with AI automation and advanced decision models, it creates a class of threats that are both highly effective and difficult to detect with traditional tools.
Defending against this requires:
- Multimodal detection (software + hardware + server behavioral signals).
- Visual analysis and AI-driven pattern recognition like Waldo.
- Platform level controls and anti-tamper protections.
- Human in the loop adjudication to handle ambiguous cases. DMA cheats are not the end of fair play, but they raise the bar for anticheat architecture and make clear that detection must evolve beyond process signatures to include output semantics and hardware aware threat signals.
